TLDR
- World Liberty Financial token holders losing WLFI to hackers exploiting Ethereum’s EIP-7702 upgrade
- Attackers pre-plant malicious smart contracts in wallets after stealing private keys through phishing
- Users report saving only 20% of tokens in emergency transfers before hackers drain remaining funds
- Exploit activates when users deposit ETH for gas fees, triggering automatic token theft
- Official WLFI team warns users about fake support messages and copycat scam tokens
World Liberty Financial token holders are falling victim to a sophisticated phishing attack that exploits Ethereum’s recent EIP-7702 upgrade. Security expert Yu Xian from SlowMist has identified multiple cases where WLFI tokens are being drained from compromised wallets.
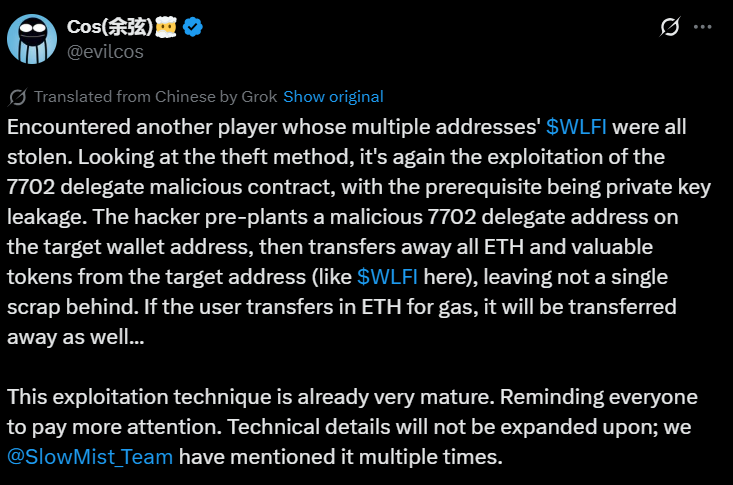
The attack method targets the EIP-7702 feature introduced in Ethereum’s Pectra upgrade. This upgrade allows external accounts to temporarily function as smart contract wallets, enabling batch transactions and delegated execution rights.
Hackers first compromise user private keys through phishing campaigns. Once they gain access, attackers pre-plant malicious smart contracts into victim wallet addresses connected to the stolen keys.
The Theft Process Explained
The exploit remains dormant until users attempt to deposit ETH for transaction fees. When the deposit arrives, the malicious contract automatically activates and transfers all tokens to hacker-controlled addresses.
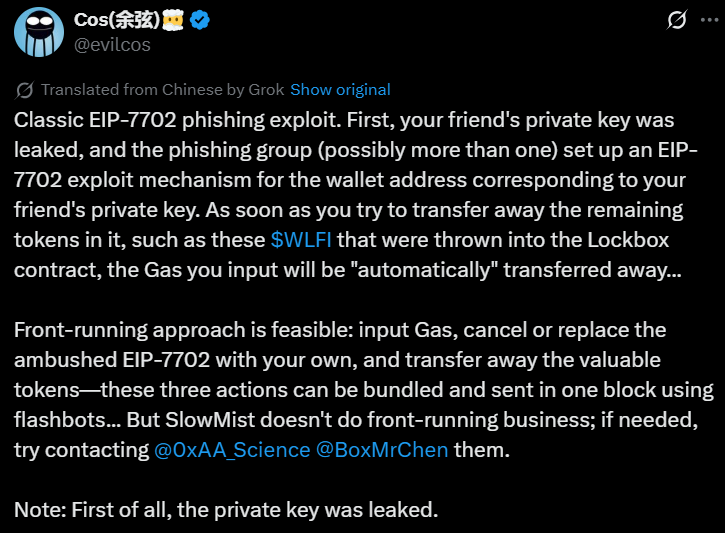
Xian documented cases where multiple wallet addresses belonging to the same victim were compromised. Each theft followed the identical pattern using the delegated malicious contract method.
World Liberty Financial launched on Monday with 24.66 billion total tokens. The Donald Trump-backed project immediately became a target for various scam operations.
One user reported their friend’s WLFI tokens disappeared after transferring Ether into their wallet. Xian confirmed this matched the classic EIP-7702 phishing exploit pattern.
Victim Reports and Forum Discussions
WLFI community forums contain multiple theft reports from affected users. One member using the handle hakanemiratlas described losing 80% of their token holdings to the exploit.
They managed to rescue only 20% through emergency transfers while racing against hackers. The user described the process as extremely stressful, with even gas fee deposits risking immediate theft.
Another forum user named Anton explained why many holders face this vulnerability. The WLFI presale requires participants to use the same wallet address that joined the project whitelist.
Anton requested the development team implement direct transfer options to prevent automated sweeper bots from stealing tokens upon delivery.
Security Warnings and Scam Prevention
Xian suggested potential solutions including canceling malicious EIP-7702 delegations and replacing them with user-controlled contracts. However, this requires successfully executing transactions before hackers respond.
Analytics firm Bubblemaps identified multiple fake WLFI contracts designed to deceive users. These “bundled clones” mimic legitimate crypto projects to steal funds.
The official WLFI team issued warnings about fraudulent support contacts. They confirmed never contacting users through direct messages on any platform.
Users should only trust official email communications from verified domains. The team emphasized carefully checking sender addresses before responding to any messages.
Multiple theft reports continue as the exploit targets additional WLFI holders with compromised wallets.





